All Blogs
8 Steps For IAM System Audit
As organizations grow and evolve, the importance of maintaining a robust and flexible Identity Access Management (IAM) system becomes ever more critical. Organizations that neglect […]
All Blogs

As organizations grow and evolve, the importance of maintaining a robust and flexible Identity Access Management (IAM) system becomes ever more critical. Organizations that neglect […]

Table of Contents Introduction DevSecOps is a critical component of modern software development, enabling organizations to build secure, reliable, and efficient software systems. Financial clients, […]
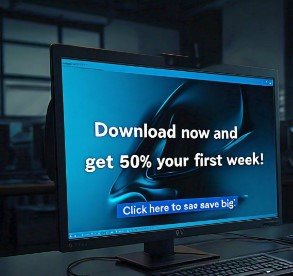
Cause : Malvertising (malicious advertising) is the use of online advertising to spread and install malware or redirect your traffic. Cybercriminals inject infected ads into […]

1) Cloud ThreatsAs remote work and online collaboration intensified during the coronavirus pandemic, cloud adoption has emerged as an ally for enterprises to ensure business […]

Being a CTO or a CIO today is tougher than ever. As if aligning IT with overall business strategy while keeping pace with rapidly changing […]
Copyright © 2024 | WordPress Theme by MH Themes